- Turbine Controller
- Wind turbine cannot work properly without accurate controls
- monitors safe operation of turbine
- takes action to correct faults, change electrical loads, and manage startup and shutdown
- Mechanical and Electrical parameters much match for the balance of power in turbine
- Mechanical
- rotor speed
- torque on rotor
- power
- blade pitch control/pitch angle
- Electrical Parameters
- Voltage
- Frequency
- generator speed
- Can be designed for upwind or downwind configuration
- downwind turbines have self-alignment passive yawing
- Modern turbines have active yawing
- rotate nacelle with respect to the tower
- operating characteristic curve determines the power output at each wind speed
- look-up table in the turbine control system
- Wind Speed measured by anemometer
- smaller wind turbines work based on stall control
- power capacity lowers as wind speed increases beyond certain value
- Park position using turbine brakes
Friday, November 30, 2012
Notes - Chapter 10 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
Notes - Chapter 9 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- Gears are used to change the speed and torque between two shafts
- driving shaft is the input
- driven shaft is the output
- usually used as speed reducers, torque on output shaft larger than input torque
- In wind turbines gears increase the speed of rotor to match higher speed of electric generators
- Configurations for a pair of gears
- Spur Gears the shaft are parallel
- bevel gears shafts are perpendicular
- worm gears shafts are perpendicular
- Gears can be categorized based on the angle of the teeth with the body of the gears
- helical gears have teeth cut an angle
- Backlash is the free play between a pair of gears
- optimally want to minimize
- Planetary Gears
- sets of gears with a particular arrangement
- Sun Gear
- output
- Ring Gear
- often stationary and doesn't rotate
- Planet Gear
- Arm
- input
- Gears can be combined in a gearbox, planetary gear combined with other gears
- Lubrication is vital reduces friction, cooling, moves dirt and debris away
- Alignment is also crucial
- Damage leads to permanent failure
- types of damage are fracture, bending, wear, fatigue, cracks, and scuffing
Notes - Chapter 8 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- P = IV
- Loads
- Resistive load is a load due to resistors and not dependent on frequency
- Capacitors and Inductors exhibit frequency dependent resistance called reactance
- Capacitive and Inductive loads act in opposite directions in phasor diagram can cancel each other's effect
- cause phase difference between voltage and current
- preferred value for the phase angle should be as close to zero as possible
- power factor is the value of the cosine of phase angle
- electric motors put both inductive and resistive loads into circuit
- Capacitors in parallel with motors reduce inductive load
- Current Leading Voltage, means current waveform reaches max or min value before voltage waveform
- Power types
- DC power corresponds to resistive load
- AC
- reactive power
- corresponds to inductive and capacitive loads
- power stored in each half cycle and sent back to circuit
- active power
- resistive loads in AC
- real power that converts heat or work
- apparent power
- provided to maintain a current I in a circuit of voltage V, generator provides apparent power
- To connect turbine to a grid
- equal voltages
- same frequency
- synchronized waveforms
- have similar phase sequences
- Turbine must not lower the power factor of grid
- The output from all turbines in a wind farm goes to collector substation
- raises voltage from turbines to grid
- Power quality
- perfect sinusoid in AC circuit
- no fluctuations in voltage and frequency
- variations, flickers and spikes all indicate lack of quality
- Harmonics are low-voltage signals that are multiples of the frequency
- Islanding when a wind farm becomes isolated from the rest of the network which can lead to a drift and voltage and frequency
- Control actions
- control voltage
- control frequency
- control available current due to power from wind
Notes - Chapter 7 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- Power is proportional to force required to move it and how fast the object moves
- can be proportional to torque and angular speed for rotational objects
- Power grasp from wind of a turbine is affected by how fast the turbine rotates and the pitch angle of blades
- relationship between power grasp and angular speed is not linear
- TSR is Tip speed ratio, ratio of tip of blade speed to wind speed
- depends on wind speed and turbine angular speed
- Power grasp depends on power coefficient not constant for turbine
- Turbine must operate at a speed where the power coefficient is around maximum value
- Daily production of turbine
- based on pattern of wind over 24 hr
- power multiplied by time for various values of turbine power
- Annual production is daily production multiplied by operating days while accounting for effect on density and temperature based on season
Notes - Chapter 6 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- Electrical Machines
- Generator converts mechanical energy to electrical energy
- works based on Lorentz Force, wire moves inside magnetic field generating voltage
- Motor converts electrical energy to mechanical energy
- works based on Lorentz Force, current carrying wire inside magnetic field has a force exerted on it
- AC and DC machines cannot operate interchangeably
- DC generator connections must have same voltage
- AC Generator connections must have same frequency, and synchronized
- Fluid Analogy
- Electrical voltage is a measure of the level of electricity
- Current is a measure of the flow of electricity
- Loads consume electricity, slow the flow, and or reduce the level
- Source provides electricity or provides movement/flow
- AC frequency is measured in Hz
- North America power is provided at 60 Hz
- European countries power is provided at 50 Hz
- Voltages of loads and sources must match
- Power capacity of source must be greater than the power of loads
- Frequency of load to source must be the same
- important for attaining required rpm for motors
- (PM) Permanent Magnets are not often used, usually electromagnets
- right hand rule
- DC motor can have any acceptable rpm, AC motor can have speeds at synchronous or close to synchronous speed, dependent on frequency of electricity provided
- generators can be connected together
- Wind Turbines don't generate power when wind speed is below cut-in speed, and does not generate electricity over cut-out speed
- during strong winds wind turbine can be taken out of service, stopped and brakes applied
Back to ToC
Notes - Chapter 5 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- main components of a wind turbine are
- tower
- newer are cylindrical, sometimes with a taper
- older are lattice towers
- nacelle
- housing on the top of tower
- provides room for gearbox, generator, and other misc components
- rotor
- moving part, consists of blade and hub
- foundation
- heavy concrete foundation to endure wind
- Each wind turbine has a transformer to usually increase the voltage of electricity produced by generator
- pad-mount transformer
- All turbines have anemometer that measures direction and speed of wind
- sometimes wind direction is detected with a separate device
Notes - Chapter 4 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- Wind Turbine Types
- Horizontal Axis
- HAWT
- must be yawed into the wind for max wind capture, follow wind direction
- most common wind turbine is propeller wind turbine, works based on lift force
- Vertical Axis
- VAWT
- not sensitive to wind direction
- easier accessibility to most of the components
- Darrieus Machine
- weak starting torques
- good power coefficients
- H-Rotor
- weak starting torques
- good power coefficients
- Savonius Rotor
- drag-type turbine can be installed as either VAWT or HAWT
- drag-type turbines have smaller power coefficients
Notes - Chapter 3 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- Any object in the wind stream subject to a force from wind
- Force an object depends on the form and size of the object
- Force can result in torque
- Force can be measured in pounds
- Torque in foot-pounds
- Forces are represented with vectors
- force on a plate from wind depends on angle between plate and wind direction called angle of attack
- aerodynamic forces include
- drag
- drag coefficient is ratio of drag force to aerodynamic force
- lift
- ratio of lift force to aerodynamic force
- airfoil is a long thin object with a large lift coefficient but a small drag coefficient
- leading edge confronts air
- trailing edge leaves air
- chord the width between the leading edge and trailing edge that is larger than the average thickness
- chord line is the straight line between leading and trailing edge
- gradual curves round leading edge, sharp trailing edge
- low thickness to chord ratio
Notes - Chapter 2 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- Energy is the potential to do work
- any moving object has some kinetic energy
- energy depends on mass and velocity squared
- Flowing Fluids also contain kinetic energy
- based on density
- cross-sectional area
- speed cubed
- If in a pipe cross section restricts area, if in free moving air we define a cross section
- Power is more meaningful than energy
- Energy in 1sec
- Energy is Power multiplied by time
- Power Absorption depends on power in the wind and the power coefficient of the turbine
- Maximum value is called the Betz Limit
- 16/27 or 0.59
- Wind speed is not constant
- varies from hour to hour season to season
- varies with height
- wind pattern needs to be investigated
- represented by graph
- changes with terrain
- top of a hill has greater wind speed than in a valley
Notes - Chapter 1 Summary
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- Wind has been a source of energy since ancient times
- Persian Windmill Vertical Axis, 1000 years old
- Dutch Windmill Horizontal Axis, built in 12th century
- Early wind turbines much smaller than modern turbines
- 4 MW
- Earth has limited resources that must be balanced
- Sufficient wind energy in the world to power everything but has difficult to use energy load
- wind turbines have small production capability
- requires smart grid to allow electric network to compensate for any additional loads or additional production
- Electric Energy measured in KW hours
- CO2 generated .712 kg per kw-hr
- Wind development requires good wind profiling
- wind speed increases with height
Notes - New and Future Technologies
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- energy must be able to transmitted
- dispatch system
- communication by radio fax to all participants
- inform nodes about levels of production
- peak hours
- highest consumption hours
- schedule production based on consumption patterns
- distributed generation systems
- many smaller power plants rather than singular large power plants
- smart grid
- controlling load and production efficiently through managing distributed systems
- automated controls and supervising
Notes - Wind Turbine Siting
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- siting is the evaluation of a site for wind turbines and development
- wind resource map not enough quality of wind
- quality of wind depends also on topography and altitude
- class of wind
- also have to worry about frequency of wind storms or hurricanes
| wind class | wind speed(m/sec) | wind speed(mph) |
| Marginal | 5.6-6.4 | 12.4-14.3 |
| Fair | 6.4-7.0 | 14.3-15.7 |
| Good | 7.0-7.5 | 15.7-16.8 |
| Excellent | 7.5-8.0 | 16.8-17.9 |
| Outstanding | 8.0-8.8 | 17.9-19.7 |
| Superb | 8.8-11.1 | 19.7-24.8 |
Notes - Wind Farm Development
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- wind farm sometimes called wind park
- equivalent of power plant
- area with large number of turbines
- have to scope area collect wind data
- metrological data
- met tower to collect data, vary in height form 10-70m
- studies roughly around 3 years unless historical data can be drawn
- verify transmission line
- coordinate with local authorities
- perform soil studies to ensure foundation engineering
- due to cost of studies often built with tax breaks
Notes - Technical Issues
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- disadvantages of wind energy
- low level energy not high capacity
- requires a lot of land area
- wind power ratings are for maximum power delivery
- expected max power only about 1/3rd of the day
- not continuously available
- wind cannot be the full supplier of energy for the grid in the US but is possible in other more windy countries
- transmission line technology in many of these countries not capable of supporting variable energy flows from wind energy
Notes - Importance of Renewable Energy
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- Earth has limited energy resources
- ancient times, number of people small, pollution unnoticeable, plant growth rate renewed energy resources
- modern times
- forests vanishing
- fossil fuels causing pollution
- not enough fossil fuels, small replenishment rate
- Its everyone's responsibility to care for the environment
- Modern Commodities
- heating/cooling
- transportation
- manufacturing
- Energy consumption measured in
- kilowatt hours
- coal plant per kilowatt hour generates 1.57 lb of CO2
Notes - Historical Background
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- One of the oldest forms of energy
- windmills
- water mills
- Types of windmills based on rotation axis
- vertical axis
- horizontal axis
- Generation for electricity generation 1970s
- oil crisis 1972
- Up until 1992 commercial wind turbines generated roughly 225 kilowatts
- 2002 generation grown by factor of 10
- now installations include 6183 MW wind farms
- EWEA(European Wind Energy Association)
- 2009 wind farms built total 199 offshore 577 MW
- Denmark provided 20% of its energy from wind
Notes - Introduction
The following notes are taken from Wind Turbine Technology by Ahmad Hemami.
- wind turbines are much larger than previously used
- difficult to control
- understand rules of nature and behavior
Tuesday, November 27, 2012
Paper - Rational Decision Making
Rational Decision Making:
Large Hadron Collider Scenarios
The more humans have tried to learn about nature the more they realize how little they understand. Physicist Gary Zukhov once said that, “Physicists have ‘proved,’ rationally, that our rational ideas about the world in which we live are profoundly deficient.” As an addendum we should add that the same applies to our own minds. We have to be able to make fully rational decisions when they have long lasting impacts and consequences.
Why would do we want to make rational decisions? The reason is that it’s often the most optimal choice. A rational decision is made by listing out the characteristics and consequences of a choice, and choosing the one we think is best. The primary issue here is figuring these characteristics and consequences out in complex large scale systems and decisions. Its easy if the system is small, for example, when grocery shopping, we have can make rational decisions based on the label and our tastes without drastic consequences, making it a good choice. However when the situation is more complex, and there isn’t a label we can check things become more difficult.
The first obstacle in dealing with rationality is simply the lack of information, or the presence of misinformation. For example, lets take the Large Hadron Collider. There was opposition raised against it by the many doomsday scenarios that it could create. Perhaps most famously the idea that the Large Hadron Collider can create black holes that would destroy the world. Now from a physics perspective, we can realize and calculate that the black holes created will be so small that it will almost immediately evaporate due to Hawking Radiation. This is the process where the spontaneous formation and destruction of particles occur along the edge of a black hole, resulting in one particle/antiparticle exiting the black hole, and one being sucked in, reduces the mass of the black hole causing it to evaporate.
However, Hawking Radiation as a process isn’t generally known. This is a case of the absence of information in the general public. If everyone readily knew about Hawking radiation it would be clear that this threat is not an issue. Since this isn’t the case, it can cause people to over evaluate the dangers of the Large Hadron Collider leading to an irrational risk/benefit analysis.
Another issue linked to this scenario are the problems of anchoring and overconfidence. Many people envision a black hole as an infinitely absorbing object that just gets larger and larger at a rapid rate. This has been popularized from various science fiction movies and most people believe that a black hole is a vast absorption machines that sucks in everything around it. In reality, although its impossible to escape a black hole, it doesn’t grow as actively as it is seen in the movies. We know that there are many black holes in the universe so theres no way we could exist if they were as terrible as they are depicted in the movies. For example, if the Sun turned into a black hole, although we would notice the lack of light in 8 minutes, the orbits of the planets wouldn’t change.
This anchoring occurred because of the way in which the human mind works. Most people's first experience with a black hole is in the form of a movie. Since it was our first experience with this object, it is the most easily recalled and anchored in our memory in that way. This anchoring is due to the availability heuristic. A heuristic is an experience based method towards problem solving. The availability heuristic is when we make a decision based on the easiest event that we can recall. In this case, its much easier to recall the vivid dramatic events in a movie, over something that can be learned in a classroom, or through scholarly articles.
The lack of information in the general public combined with misinformation caused by the availability heuristic could easily have led government officials to make an irrational decision regarding the Large Hadron Collider to shut it down. Now we actually haven’t done extensive analysis on what the risks/benefits of the LHC are worth but this is already considered an irrational decision because it was motivated by incorrect information.
This hypothetical situation leads us to another aspect in making rational decisions, recognizing feedback loops. There are powerful information and societal feedback loops inherent to our society. Lets say the media spreads the word for the potential of world destruction due to the Large Hadron Collider. This initial spread of information could affect people in high ranking positions in a socio political group. In this example lets take the theological example of high officials in the church. If these officials change the church’s official stance on the Large Hadron Collider the media will publicize it as one of their sources. This leads to more to more reports being made on the subject, which could reinforce the stance of the church, reinforcing the stance of the media, so on and so forth. This is an example of how even an initially incorrect or false claim can grow itself into a large multi group movement.
The above scenarios all deal with the lack of information or misinformation and how it can spread to become a threat to rational decision making. The next case deals with how we process information. When we consider a complex project like the Large Hadron Collider, we have to take into account more the risks and benefits than just discovering the Higgs boson and the potential to create black holes. We also have to consider it as an engineering project and make decisions based on a sustainability standpoint.
We can go through a few calculations here. It took about 4.75 billion dollars to construct the LHC, the electricity costs run about $23.5 million per year, and requires an operating budget of 1 billion dollars. This is a huge economic investment. Depending on the location this could cause huge issues, for example if the LHC was built in a rural 3rd world country so that it’d be physically out of the way from first world countries, it could devastate that locations economy as its resources gets forced into one project. Likewise we also have to consider its yearly costs, taking into account that the average cost for electricity in Europe is about 17 euro cents a kilowatt, we can calculate that the collider uses up about 150 million kilowatts a year. This is enough to power about 12,000 homes. Again this could be a huge burden on the host country for this project depending on how wealthy they originally were.
In reality, the Large Hadron Collider was built in Switzerland which has good low emission production of electricity, and so the environmental cost in greenhouse gases for the LHC is only about 700,000 kg of CO2. Now, we can weigh this in both an economic and ethical sense. Assuming we view progress as a worthy goal we can think that these costs seem to be fairly reasonable for the possibility for completing the standard model of particle physics which leads to development in every aspect of almost all sciences. On the other hand considering the costs would this money have been better spent towards alternative energy development or medical research towards curing cancer? This are the things we have to consider in order to make the decision fully rational by obtaining the correct information and processing it in all aspects socially, economically, and ethically. So as we can see there are many different obstacles when it comes to making rational decisions. The issues range from spreading correct information to recalling appropriate information, from recognizing trends in a system, to determining what is the correct choice. However, although these topics may seem disparate, we can address them all in the same way, through education. One of the aspects of education is distributing correct information in a way which is easy to recall which addresses the first two obstacles. Recognizing trends and making appropriate choices is comparable to learning appropriate problem solving techniques, which is the other aspect of education. The last aspect of our education is in our values as a person. We have to consider whether or not our decisions are ethical and work towards a social good, which again we grow through not only our official education but simply through experiencing life. When we consider and weigh all these aspects we can then make rational decisions that benefit us all.
Sunday, November 25, 2012
Archery - Tournament Practice Scores 1
Archery Lessons Scoring Practice
| Andrew | Austin | Edward | Esam | Johanna | Tabib | |
| 18 Meters, 40 cm Target, 30 Arrows | 126, 122, 144, 115 | 149, 124, 129 | N/A | N/A | 37 | 85 |
| # of Arrows Shot | 72, 84 | 78, 66 | N/A | N/A | 54 | 54 |
| Running Total | 508 | 273 | N/A | N/A | 37 | 85 |
| Tournament Total 120 Arrows | 508 | N/A | N/A | N/A | N/A | N/A |
Saturday, November 24, 2012
Trivia - A Google a Day LXIII
Beenalaght, in the county of Ireland that includes the city of Mallow, is an example of what?
Stone Row
What artist accompanied Cook on his second expedition and produced notable paintings like "Tahiti Revisited, 1776"?
William Hodges
Who is the first winner of College Football's Heisman Trophy to have gone on to become a professional in the NBA?
Charlie Ward
As of 2012, in what county is the third busiest airport in the country of which "Amhran na bhFiann" is the national anthem?
Clare
According to Walter J. Fraser's book, what path out of Charleston was "bumper-to-bumper" by noon on September 21, 1989?
Interstate 26
What is the citizenship of the star signed to RBMG shortly after it was created in 2008?
Canadian
Who is the wife of the giggling, iconic character, originally created by Chet Noice and debuted on television in 1965, that springs to life from ready-to-bake dough?
Poppie Fresh
Which NHL legend was born on the exact same day as the singer with multi-Platinum Heavy Metal band Cinderella?
Wayne Gretzky
What character from Greek Mythology does Eve mimic when she is sad and sitting by the pond in Mark Twain's account of her experiences?
Narcissus
Which MLB catcher shares his name with a former NFL quarterback and an Emmy-winning, Chicago-based news anchor?
Rob Johnson
Stone Row
What artist accompanied Cook on his second expedition and produced notable paintings like "Tahiti Revisited, 1776"?
William Hodges
Who is the first winner of College Football's Heisman Trophy to have gone on to become a professional in the NBA?
Charlie Ward
As of 2012, in what county is the third busiest airport in the country of which "Amhran na bhFiann" is the national anthem?
Clare
According to Walter J. Fraser's book, what path out of Charleston was "bumper-to-bumper" by noon on September 21, 1989?
Interstate 26
What is the citizenship of the star signed to RBMG shortly after it was created in 2008?
Canadian
Who is the wife of the giggling, iconic character, originally created by Chet Noice and debuted on television in 1965, that springs to life from ready-to-bake dough?
Poppie Fresh
Which NHL legend was born on the exact same day as the singer with multi-Platinum Heavy Metal band Cinderella?
Wayne Gretzky
What character from Greek Mythology does Eve mimic when she is sad and sitting by the pond in Mark Twain's account of her experiences?
Narcissus
Which MLB catcher shares his name with a former NFL quarterback and an Emmy-winning, Chicago-based news anchor?
Rob Johnson
Friday, November 23, 2012
Notes - Error Detection and Correction
The following are notes from Computer Networks written by Tanenbaum 5th edition.
- Communication channels have a wide range of characteristics
- We must have a way to deal with errors
- error correction codes
- FEC(Forward Error Correction)
- error detection codes
- both must account for the types of erros that can occur, both have trade offs
- burst error
- single bit error
- sometimes location of an error will be known, erasure channel
Error - Correcting Codes
- four different codes
- Hamming Codes
- Hamming distance, the number of bits that are different between two sequences after exclusive or each bit together
- to reliably detect d errors you need a distance d+1 code
- total length of a block is n = m + r
- n bit code word
- code rate is the fraction of a codeword that carries non redundant information
- example
- 0000000000, 0000011111, 1111100000, 1111111111
- hamming distance of 5 so can correct double errors or quadruple errors
- useful for understanding block codes
- Binary Convolution Codes
- convolution code, no natural size, as incoming bits come in perform some operation
- each input bit produces two output bits on the right hand side that are XOR sums of the input and internal state
- each state is kept in 6 memory registers, each time another bit is inputted all values are shifted to the right, constraint length of this code is k = 7
- Viterbi algorithm
- soft decision decoding determine likeliness of 1, 0
- hard decision decode determine each bit is 0,1 before error correction
- Reed - Solomon Codes
- linear block codes, systematic
- operates on m bit symbols
- based on fact that every n degree polynomial is determined by n + 1 points so if 2 points are received in error, we can find the third point that will still lie on the line
- defined as polynomials that operate over finite fields, strong error correction properties makes them useful in DSL, CDs, DVDs and Blu-Ray
- Low - Density Parity Check Codes
- LDPC (Low - Density Parity Check Codes)
- each output bit is formed from only a fraction of the input bits
- matrix representation of code with low density of 1s, standard for video broadcasting, 10 Gbps Ethernet and 902.11
- these all add redundancy to the information that is sent
- systematic code, m data bits are sent along with check bits
- linear code check bits are computed as a function of the data bits
- usually using exclusive or
Error - Detecting Codes
- types of codes
- Parity
- parity bit appended to the end of data to make the number of 1s in the codeword even or odd
- 1011010 is sent in even parity it will be sent as 10110100 to signify that its already even by appending the 0
- can only reliably detect single bit error
- interleaving, can have multiple parity bits n x n matrix with parity bits at the end of each
- n+1 burst will still be undetected but now capable of correcting bits
- Checksums
- 16 bit internet checksum used as part of IP
- one's compliment arithmetic
- CRCs(Cyclic Redundancy Checks)
- polynomial code, treats bits as polynomial coefficients
- sender and receiver agree upon generator polynomial G(x) in advance
- algorithm
- let r be degree of G(x) append r zero bits to the low order end of the frame so its now m+r bits
- divide the bit string corresponding to G(x) into the bit string using modulo 2 division
- subtract the remainder using modulo 2 subtraction, the result is checksummed frame to be sent
- example as follows
- with single bit or 2 single bit errors the division will not be able to grant the same checksum if burst length is r+1 the remainder will be zero if and only if the burst is identical to G(x)
- IEE 802 standard is
- detects all bursts of length 32 or less and all bursts that are odd
Notes - Data Link Layer Design Issues
The following are notes from Computer Networks written by Tanenbaum 5th edition.
- Data link layer uses services of the physical layer to send and receive bits over communication channels
- provide a well defined service interface to the network layer
- deal with transmission errors
- regulate flow of data so that slow receivers are not swamped by fast senders
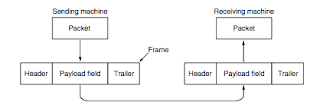
- data link layer takes packets and encapsulates them into frames for transmission
Services Provided to the Network Layer
- function is to provide services to the network layer
- path data takes shown below
- offers various services
- unack connectionless service
- source machine send independent frames to destination machine
- ack connectionless service
- WiFi (802.11)
- ack connection oriented service
- most sophisticated, source and destination establish reliable data link
Framing
- in order to provide services to network layer, it must use the services provided by the physical layer
- must break up the bit steam using
- Byte Count
- uses a field in the header to specify number of bytes in frame
- can be garbled by transmission error
- rarely used on its own
- Flag Bytes with byte stuffing
- flag bytes used as starting and ending delimiters
- byte stuffing
- sender's data link layer insert a special ESC(escape byte) before each accidental flag byte
- following is an example used in PPP(Point to Point protocols)
- Flag Bits with bit stuffing
- gets around byte stuffing disadvantage that it is tied to 8 bit bytes
- can contain arbitrary bits developed for HDLC(High Level Data Link Control Protocol)
- Physical Layer coding violations
- is a shortcut from the physical layer
- if we do 4B/5B we don't need to map to all possible symbols so the unused signals are violations that signal an error
Error Control
- mark the start and end now we have to see if delivery is in order
- provide sender with some feedback
- introduce timers into data link layer, starts a time so that frame is set to expire
- this way sender knows if frame has been lost
- issue to manage timers
Flow Control
- what to do when a sender wants to transmit frames faster than receiver can accept them
- two approaches are commonly used
- feedback-based flow control receiver sends information to sender to give permission to send
- rate based flow control, built in mechanism to limit rate of sending
- NIC(Network Interface Cards)
- can handle frames as fast as they can arrive so overruns aren't a problem
Notes - Data Link Layer
The following are notes from Computer Networks written by Tanenbaum 5th edition.
- VLANs(Virtual LANs)
- connections called bridges to join lans together
Uses of Bridges
- Reasons why an organization may have multiple LANs
- Many university and corporate departments have their own LANs
- Organization geographically spread wants to be joined
- Split a single LAN into separate LANs for logical organization
- bridges let LANs be joined while keeping their own capacity
- bridges increases reliability
- can reroute nodes that are malfunctioning giving garbage data
- transparent bridges
- create with backward learning algorithm to stop traffic from being sent to unneeded areas and spanning tree algorithm to break loops
Learning Bridges
- example topology
- bridges developed when classic ethernets were in use
- bridge operates in promiscuous mode accepts every frame to its ports
- chooses to forward or discard
- simple way to implement this scheme is to have a big hash table
- initially empty
- backward learning every frame sent tells the bridge about the topology
- arrival time of frames noted in entry, tells the bridge the last time a frame is seen
- bridge scans and purges entries more than a few minutes old
- routing procedure for incoming frame
- if the port for destination is same as source discard frame
- if destination port is different from source forward to destination
- if destination unknown send frame on all ports except the source
- as each frame arrives algorithm must be applied
- cut through switching/wormhole routing
- bridges only look at MAC addresses to reduce latency
Spanning Tree Bridges
- to increase reliability redundant links used between bridges
- this introduces loops in the topology
- so in order to do this, overlay the topology with a spanning tree to reach every bridge, ignore some links, example as follows
- spanning tree is built with distributed algorithm, bridge periodically broadcasts a configuration message on all ports
- tree of shortest paths from root to every bridge constructed, and spanning tree used between bridges
- Radia Perlman poem
Repeaters, Hubs, Bridges, Switches, Routers and Gateways
- These devices operate in different layers which is why even though they perform similar roles, they are all necessary
- repeaters amplify signals
- hubs don't amplify, but allow for multiple lines
- bridges connects two or more LANs has multiple ports
- isolated in its own collision domain, CSMA/CD not needed
- better performance than hubs
- can join different types of LANs such as Ethernet and Token Ring
- joins different max frame lengths
- join different security protocols
- switches are modern bridges by another name
- utilizes twisted pair cables, often used for ethernet
- routers totally different
- frame header and trailer gets stripped off and the packet located in payload field is passed to routing software
- chooses outgoing line with address
- does not see fram address or where packet comes in on
- transport gateways connect two computers using different connection oriented protocols such as
- TCP/IP
- SCTP
- understands formats such as email into sms messages
Virtual LANs
- issues
- difficult to replace, geographically new workers have to sit at open workstations instead of with their coworkers
- load issue not even
- broadcast traffic to reach correct persons
- vulnerable to broadcast storm when LAN malfunctions and sends random messages
- solution is to set up VLAN(Virtual LAN)
- based on VLAN aware switches
- network admin decides how many VLANs are possible
- association as configuration tables are built into bridges
- The IEEE 802.1Q Standard
- To implement this scheme bridges need to know which VLAN an incoming
- issues
- do we need to throw out existing ethernet cards to accomodate this standard?
- who generates fields?
- what happens to max size frames
- VLAN fields are only used by bridges and switches and not by user machines
- bridge is also allowed to use higher layer protocol to select colors for VLAN creation
- for 802.1Q Ethernet frames, the tag composed of
- 3 bit priority field
- CFI(Canonical Format Indicator)
- indicate order of bits in MAC adress
- VLAN Identifier specifies color of VLAN
- when this comes to VLAN aware switch the identifier is matched to a table to figure out which ports it should send to
Notes - RFID
The following are notes from Computer Networks written by Tanenbaum 5th edition.
- RFID(Radio Frequency Identification)
- EPC(Electronic Product Code)
- commercialized by EPCglobal
EPC Gen 2 Architecture
- communicates via the RFID Reader which sends out a signal that gets scatted back by a RFID tag
- EPC gives each tag 96 bit EPC identifier
- readers have all the intelligence, much more powerful and do all signal processing
EPC Gen 2 Physical Layer
- sent in the UHF(Ultra High Frequency) range
- readers and tags use ASK(Amplitude shift keying) modulation to encode bits
EPC Gen 2 Tag Identification layer
- situation is multiple access problem
- closest protocol is slotted ALOHA protocol
- tags pick a random slot to reply with
- sends a short 16 bit random number for collision reader receives and sends ACK to acquire slot and send EPC identifier
- adjust number of slot, reader can send QAdjust message to change slot adjust level for RFID tags
Tag Identification Message Formats
- Form of the Query Message
- Command field identifies this as query
- DR, M, TR determine physical layer parameters
- Sel, session and target select the tags to respond tags keep track of up to 4 concurrent sessions
- Q defines the range of slots that tags can respond to 0 to 2Q-1
- CRC to protect the fields
- grown to resemble very small computers Internet of Things
Notes - Bluetooth
The following are notes from Computer Networks written by Tanenbaum 5th edition.
- developed by Ericsson, IBM, Nokia, Intel, and Toshiba in a SIG(Special Interest Group)
- bluetooth utilizes pairing to securely transfer data between mobile devices
Bluetooth Architecture
- piconet a master node with up to seven slave nodes
- multiple piconets can be connected into a scatternet
- up to 255 parked nodes in a set, master set these devices into a low power state to reduce drain on batteries
- at its heart is a TDM system
Bluetooth Applications
- most network protocols provide channels
- Bluetooth provides applications called profiles
- 6 are for audio and video
- human interface profile such as keyboards and mice
- profiles for networking
- personal area network profile, ad hoc network or remote access to another network through an AP
- profiles for higher level info exchange
The Bluetooth Protocol Stack
- loose group into layers does not follow OSI or TCP/IP or the 802 model
- layer description here
- bottom layer is the physical radio layer
- link control is baseband layer similar to MAC sublayer with some physical layer
- two protocols to use link control
- link manager
- establishment channels, pairing and encryption, QoS
- below the line implemented on the chip
- L2CAP(Logical Link Control Adaptation Protocol)
- frames variable length messages and provides reliability as needed
- many protocols use this
- Top layer is where applications are located
- profiles are vertical boxes because they define a slice of the protocol stack
The Bluetooth Radio Layer
- radio layer moves bis from master to slave, operating range 10 meters
- uses adaptive frequency hopping
- 3 forms of modulation used to send bits
- frequency shift keying to send a 1 bit symbol every microsecond
- 2 or 3 bit enhanced rates introduced in 2.0 used for only data portion of frame
The Bluetooth Link Layers
- link control or baseband layer close to MAC
- turns the raw bit stream into frames and defines formats
- piconet defines 625 microsecond time slots
- frames 1, 3, 5 slots long
- overhead of 126 bits for access code and header, settling time of 250-260 microseconds per hop to allow for stability
- 5 slot frame much more efficient than 1 slot frame
- link manager sets up channels called links using pairing procedure, configured with same PIN(Personal Identification Number)
- SCO (Synchronous Connection Oriented)
- used for real time data
- fixed slot in each direction
- ACL (Asynchronous Connectionless Link)
- used for packet switched data
- sent over L2CAP layer
- accepts packets of up to 64KB from upper layers breaks them into frames
- handles multiplexing/demultiplexing of multiple packet sources
- handles error control and retransmission
The Bluetooth Frame Structure
- defines several formats, two types of frames
- Header field
- Adress identifies which of the 8 active devices we can go for
- type identifies ACL, SCO, poll, or null
- Flow assert by slave when buffer is full
- ack is for acknowledgements
- Sequence is to number the frames for transmission, since its stop and wait protocol only need one bit
- 8 bit checksum
- entire header repeated 3 times for error correction, if all 3 same received, if not majority option is accepted
- data field has its own formatting
Notes - Broadband Wireless
The following are notes from Computer Networks written by Tanenbaum 5th edition.
- Broadband wireless, large antenna on a hill easier than digging many trenches for cables
- 802.16 WiMAX(Worldwide Interoperability for Microwave Access)
- fairly complicated like OSI so there is a WiMAX forum to define standards
Comparison of 802.16 with 802.11 and 3G
- why not just use 802.11 or 3G?
- more akin to 4 G combines both aspects
- connect devices to internet at megabit/sec speeds without cable or DSL
- designed to
- carry IP packets over air
- peer to peer VoIP stream media
- OFD based technology
- more like 3G in that
- tries to achieve high capacity
- uses more power and better antennas
- licensed spectrum around 2.5 GHz
- LTE(Long term evolution)
- collision course with 4G
The 802.16 Architecture and Protocol Stack
- base stations connect directly into backbone network, air interface to mobile and subscriber stations
- the following is the protocol stack
The 802.16 Physical Layer
- utilizes 3.5 GHz or 2.5 GHZ
- transmissions over OFDM
- Symbols are sent with QPSK, QAM-16, QAM-64
- SNR ratio in order to reach distant stations use QPSK sends 2 bits per symbol coded for forward error correction
- common for noisy channels to tolerate bit erros
- 802.16 developers did not like certain parts of GSM and DAMPS
- chose flexible scheme OFDMA(Orthogonal Frequency Division Multiple Access)
- different sets of subcarriers so that more than one station can send/receive at once
- also chose to use TDD(Time Division Duplex) to alternate between sending and receiving
- could have done FDD(Frequency Division Duplex) but this is not as flexible and harder to implement
- one of new uplink bursts reserved for ranging
- process by which new stations adjust timing and request initial bandwidth during base station setup
- is a hope and transmit setup assumes no collision
The 802.16 MAC Sublayer Protocol
- data link layer divided into 3 sublayers
- encryption to keep data secret
- perform mutual authentication using RSA public-key cryptography using X.509 certificates
- Uplink Channel Services
- Constant bit rate service
- transmit voice
- Real-time variable bit rate service
- transmit multimedia
- Non Real-time variable bit rate service
- file transfer
- Best effort service
- everything else
- ethernet binary exponential backoff algorithm used
- all are connection oriented
The 802.16 Frame Structure
- All MAC frames begin with generic header, followed by CRC
- checksum surprisingly optional since no attempt is made to retransmit
- Generic Frame
- EC bit tells whether payload is encrypted
- type identifies frame type
- tells whether packing and fragmentation are present
- CI indicates presence or absence of checksum
- EK tells which encryption is being used
- length gives complete length of entire frame
- connection identifier tells which connection this frame belongs too
- Header CRC uses polynomial x8 + x2 + x + 1
- Bandwidth request frame is different, starts with 1 bit instead of 0 and is just a command
Trivia - A Google a Day LXII
On what surface did Camille Pissarro render his 1885 depiction of the Gisors market?
Paper
As of 2012, which is the only NBA team named after an insect?
New Orleans Hornets
As of 2011, who is the only Canadian ever to have won one of Golf's Majors?
Mike Weir
Because Union officers thought him disloyal, the property of the commander of the Confederate Army was appropriated to create what burial ground?
Arlington National Cemetery
Who loaned Lee Krasner and her husband the money for the downpayment on a property with a house and barn in Springs on Long Island, New York?
Peggy Guggenheim
In 2011 researchers found a new way to test for Multiple Sclerosis. What element of the patient will be tested?
Patient's Breath
Whom did John Phillips not want in his band, convinced that her size would stand in the way of the group's success?
Cass Elliot
When neophyte screenwriter Sylvester Stallone presented his heartwarming script about a potential heavyweight champion to United Artists, whom did the studio push for the lead role?
Ryan O'Neal
What body of water is the southern boundary of the country that flies a flag that is comprised of vertical bands of equal widths of orange (at the hoist), white and green?
Gulf Of Guinea
What beach in the southern region of India's smallest state (by area) is particularly crowded in October when pilgrims flock to a local church of the same name?
Colva Beach
Paper
As of 2012, which is the only NBA team named after an insect?
New Orleans Hornets
As of 2011, who is the only Canadian ever to have won one of Golf's Majors?
Mike Weir
Because Union officers thought him disloyal, the property of the commander of the Confederate Army was appropriated to create what burial ground?
Arlington National Cemetery
Who loaned Lee Krasner and her husband the money for the downpayment on a property with a house and barn in Springs on Long Island, New York?
Peggy Guggenheim
In 2011 researchers found a new way to test for Multiple Sclerosis. What element of the patient will be tested?
Patient's Breath
Whom did John Phillips not want in his band, convinced that her size would stand in the way of the group's success?
Cass Elliot
When neophyte screenwriter Sylvester Stallone presented his heartwarming script about a potential heavyweight champion to United Artists, whom did the studio push for the lead role?
Ryan O'Neal
What body of water is the southern boundary of the country that flies a flag that is comprised of vertical bands of equal widths of orange (at the hoist), white and green?
Gulf Of Guinea
What beach in the southern region of India's smallest state (by area) is particularly crowded in October when pilgrims flock to a local church of the same name?
Colva Beach
Notes - Wireless LANs
The following are notes from Computer Networks written by Tanenbaum 5th edition.
- wireless LAN standard 802.11
The 802.11 Architecture and Protocol Stack
- connect clients via AP(Access Points)
- several access points can be connected together in a distribution system
- ad hoc network also possible, computers can directly send frames to each other
- structure is as follows
- transmission techniques of frequency hopping and infrared are now defunct
- spread spectrum is now known as 802.11b
- OFDM is 802.11a
- multiple antenna techniques now caled 802.11n
The 802.11 Physical Layer
- transmission techniques make it possible to send a MAC frame over the air from one station to another
- short range radios in 2.4GHz or 5 GHz ISM frequency bands
- rate adaptation
- if signal is weak low rate can be used, if clear highest rate can be used
- 802.11b
- spread spectrum similar to CDMA but there is only one spreading code
- satisfy FCC requirement
- Barker sequence
- autocorrelation is low
- send at rate of 1 Mbps Barker sequence used with BPSK modulation to send 1 bit per 11 chips, 11 Mchips /second
- send at 2Mbps used with QPSK modulation to send 2 bits per 11 chips
- CCK(Complementary Code keying)
- 802.11a
- up to 54Mbps in 5 GHz band
- uses OFDM(Orthogonal Frequency Division Multiplexing)
- sent over 52 subcarriers
- 802.11g
- copies 802.11a operates in 2.4GHz ISM band
- 802.11n
- throughput of 100Mbps
- doubled channels to 40 MHz
- signal streams uses 4 antennas to transmit 4 streams at the same time
- separated using MIMO(Multiple Input Multiple Output) communication techniques
The 802.11 MAC Sublayer Protocol
- radios are half duplex
- avoids collision using CSMA/CA (CSMA with collision avoidance)
- station using channel sensing, exponential backoff 0-15 in the case of OFDM physical layer
- DCF(Distributed Coordination Function)
- starting backoffs early
- acks are used to infer collisions
- no central control
- PCF(Point Coordination Function)
- AP controls activity in cell like base station
- in practice not used
- transmission ranges of different stations may be different, exposed/hidden terminal problem
- NAV(Network Allocation Vector)
- each station keep record of when channel is in use
- how long a frame will take to complete
- Channel sensing
- RTS is right to send CTS is clear to send
- has issues, does not help short frames
- can slow down operation
- Wireless networks are noisy and unreliable
- strategies
- lower the transmission rates use more robust modulation
- if too many frames lost can lower the rate again
- probability of receiving an n bit frame entirely correctly is (1-p)n
- very difficult to receive full frame for long frame, ethernet frame has less than 30% success
- fragmentation to split packets into smaller sizes to reduce error
- power saving beacon frames
- frames advertises the presence of AP every 100 msec
- clients set a power management bit to tell it that they are entering power save mode
- will buffer traffic to power save mode nodes
- APSD (Automatic Power Save Delivery)
- sends buffer frames to clients just after client sends frames to AP
- works well for VoIP wireless phones
- QoS suffers with wireless to prevent this we have to make VoIP services higher priority
- intervals after an ack in CSMA/CA
- SIFS(Short InterFrame Spacing)
- control frame or next fragment sent here
- AIFS(Arbitration InterFrame Spacing)
- there is a high priority and low priority frame here
- DIFS(DCF InterFrame Spacing)
- regular frame
- EIFS(Extended InterFrame Spacing)
- bad frame recovery done
- TXOP or transmission opportunity
- original CSMA/CA mechanisms let stations send one at a time
- slows down fast senders to speed of slow senders
- rate anomaly
The 802.11 Frame Structure
- 802.11 standard defines 3 classes of frames
- data
- control
- management
- variety of fields used within the MAC sublayer
- Frame control made up of 11 subfields
- version set to 00 though allows future versions to be created
- type data control or management
- subtype RTS or CTS
- To DS From DS is whether the frame is incoming or going to APs
- More fragments mean more fragments will follow
- Retry is retransmission
- Power management means to go into power save mode
- More data means more frames incoming
- Protected frame means encryption has occurred
- Order tells that the frames will come in order
- Duration how long frame and ack will occupy channel
- Addresses to source and destination, 3rd can be a final destination and second is a relay point
- sequence numbers frames so duplicates can be detected
- data stores data, and check sequence is a 32 bit CRC
Services
- Association service used by mobile stations to connect themselves to APs
- Reassociation is to change preferred AP
- disassociation to break AP
- Authenticate to choose security
- recommend scheme WPA2(WiFi Protected Access 2)
- outdated scheme is WEP(Wired Equivalent Privacy)
- based on AES(Advanced Encryption Standard)
- distribution service determines routing
- integration service handles translation for frame to be sent outside a LAN
- data delivery service
- QOS traffic scheduling
- traffic with different priorities
- Transmit power control service to meat power limitations, dynamic frequency selection to avoid transmitting on reserved frequencies
Thursday, November 22, 2012
Notes - The Network Layer in the Internet
The following are notes from Tanenbaum's Computer Networks 5th Edition.
- Principles of Network Layer Design
- Make sure it works
- do not finalize until approved
- Keep it simple
- Make clear choices
- choose options rather than allowing for several ways to do the same thing
- Exploit modularity
- independent layers
- Expect heterogeneity
- Avoid static options and parameters
- Look for a good design over a perfect one
- Be strict when sending and tolerant when receiving
- Thin about scalability
- Consider performance and cost
- ASes(Autonomous systems)
- connection of internetworks
- Tier 1 networks are ISPs
- following shows connections
- IP(Internet Protocol)
- glues together internet with similarities
The IP Version 4 Protocol
- Version field keeps track of which version of the protocol datagram belongs too
- IHL is provided to tell how long the header is
- Differentiated services field changed its meaning over the years
- originally type of service field
- Total length includes the entire datagram max length 65,535 bytes
- Identification field shows the host where the packet should go, where ti belongs to
- MF is more fragments all fragments except the last one have this bit sets, lets us know when all the fragments of a datagram has arrived
- Fragment offset tells where in the current packet the fragment belongs
- TtL is used to limit packet lifetimes
- counts number of hops
- protocol tells the transport process
- header checksum crc assumed to be 0 on arrival
- source/destination address is IP address
- options field is to allow subsequent version of the protocol to include information
- security tells how secret info is, military use
- strict source routing option gives complete path
- losse source routing gives packet ability to traverse the list of routers specified
- network measurement
- record route tells each router to append its ip address to options field
- timestamp option records the 32 bit timestamp
IP Addresses
- Prefix ip addresses are hierarchal, unlike ethernet
- dotted decimal notation
- subnet mask, prefixes described by their length
- Subnets
- ICANN(Internet Corporation for Assigned Names and Numbers)
- network numbers manager
- splitting prefix example
- CIDR - Classless InterDomain Routing
- routers must be able to determine path from each source to each destination
- tables growing larger and larger
- however, can group into subnets, route aggregation
- CIDR (Classless Inter- Domain Routing)
- router routes between same prefix routers
- when packet comes in routing table is scanned to see if destination lies within prefix
- possible multiple entries will match longest prefix used
- commercial routers use custom VLSI chips with algorithms embedded into hardware
- Classful and Special Addressing
- A allows for up to 128 networks with 16 million hosts
- B allows for up to 16,384 networks with 2 million hosts
- C allows for up to 2 million networks with 256 million hosts
- 3 bears problem, since B is the only network that makes sense for scalability for a company or organization
- Class D networks are being for multicast
- NAT - Network Address Translation
- IP adress are scarce
- dynamically assign IP address to a computer when it is on
- beginning to apply to home users subscribing to ADSL or internet over cable
- problem of running out of IP addresses, solution is to move to IPv6 but this is slowly occurring
- in the meantime we use NAT(Network Address Translation)
- assign each home or business with a single ip address
- within the customer network each computer gets a unique ip address
- these addresses are unavailable
- Operation of NAT
- before packets leave a customer it passes through a NAT box that converts the internal IP to the customer's true IP address
- how does provider send back to customer?
- observed that most IP packets carry TCP or UDP payloads
- contain source destination port
- ports indicate where the TCP connection begins and ends, so we can establish port to port processes rather than ip to ip processes
- ports 0-1023 are reserved, but 1024-65,535 are available for use, so each IP gets this many ports utilized to solve the mapping issue
- issues about using NAT
- breaks end to end connectivity as an outgoing packet is necessary before incoming packets can be allowed
- home user with NAT can make TCP/IP connections to remote web server, but remote user cannot make connections to game server on home network without NAT traversal techniques
- changes from connectionless to connection oriented in an odd way
- violates protocol layering, assumes TCP operational, if TCP is upgraded to a new style, NAT will fail
- processes are not required to use TCP or UDP, if new transport protocol used, NAT cannot handle
- FTP inserts IP addresses into the body of packet, but it cannot rewrite the IP addresses here
IP Version 6
- Goals
- support billions of hosts
- reduce size of routing table
- simplify protocol
- provide better security
- pay more attention to type of service
- aid multicasting by allowing scopes to be specified
- make it possible for hosts to roam
- allow protocol evolution
- permit old and new protocol to coexist until old can be phased out
- SIPP(Simple Internet Protocol Plus) became IPv6
- The Main IPv6 header
- differentiated services distinguishes class of packets
- flow label provides way for source and destination to mark groups of packets
- payload length tells how many bytes follow header
- next header can be optional extension headers, tells transport packets such as the handler where it should pass to next
- Hop limit is Time to live, same idea
- source address destination address with 16 byte addresses
- IPv4 are designated by double collons
- address space so large it won't be used efficiently but its unlikely to run out as there are 1000 IP addresses per square meter of the earth
- Extension Headers
- IPv6 allows for jumbo payload lengths that are used to transmit gigabyte sized packets across internet
- Controversies
- address length compromise
- hop limit field limited to 255 current technology
- remove the IPv4 checksum
- reasoning is that application would have transport layer checksum anyway so no point in doing this over again
- Deployment is the difficulty with IPv6 slow conversion in small islands of IPv6
Internet Control Protocols
- ICMP(Internet Control message protocol) message types are listed as follows
- Time exceeded error message used to create traceroute utility that finds the routers along the paths to a destination, send sequence of packets with counters to reach 0 each time along the packet
- ARP - The Address Resolution Protocol
- Data link layer NICs such as ethernet cards don't understand Internet Addresses
- host 1 outputs a broadcast packet on ethernet to see who owns an IP address
- host 2 responds with its ethernet address
- defined in RFC
- gratuitous ARP
- have every machine broadcast its mapping when configured, make update or entry in everyone's ARP, if error occurs resolved by network manager
- default gateway
- router where off network traffic is sent
- possible to send packet from host to host using proxies, so unable to give direct replies, but can set a router to forward to another network
- DHCP - The Dynamic Host Configuration Protocol
- when computer is started built in Ethernet or link layer address in NIC but no IP
- broadcasts request for IP DHCP DISCOVER packet, which much reach DHCP server
- then it tells the server where it is located
- IP address assignment may be only for a fixed period of time, leasing
Label Switching and MPLS
- MPLS (MultiProtocol Label Switching)
- connection oriented network
- adds a label in front of each packet and forwarding is based on label instead of destination address
- tag switching
- Label field holds the index
- QoS indicates class of service
- S refers to stacking multiple layers
- TtL is number of hops packet can live
- MPLS enhanced packet arrives at LSR(Label Switched Router)
- label is used as an index to determine outgoing line to use
- forwarding
- finds best match for a destination address
- switching
- uses a label taken from the packet as an index into a forwarding table
- simpler and faster but not universal definition
- most hosts don't understand MPLS
- LER(Label Edge Router)
- inspects destination IP address and other fields to see what path the MPLS packet should take
- Flows that belong to the same label are called FEC(Forwarding Equivalence Class)
- traditionally not possible to group several distinct forwarding paths
- can operate in multiple levels at once
- label forwarding tables set up by
- combining routing and connection setup protocols
- when router is booted checks to see which routes for final destination
- creates FECs for each label and pass them to their neighbors
OSPF - An Interior Gateway Routing Protocol
- OSPF (Open Shortest Path First)
- became standard in 1990
- draws on IS-IS(Intermediate System to Intermediate System)
- became ISO standard
- goals
- support variety of distance metrics
- dynamic algorithm
- based on type of service
- load balancing capable
- support for hierarchical systems
- security
- supports point to point links and and broadcast networks
- abstracts collection of networks routers and links into a directed graph in which each arc is assigned a weight in terms of distance/delay
- structure routes to hosts but not through them, only through networks such as LANS
- use a link state method to compute shortest path
- ECMP(Equal Cost MultiPath)
- remembers set of shortest path and splits traffic across them equally
- AS divide itself into numbered areas where an area is a network or set of continuous networks
- routers that lie in a router are called internal routers
- each AS has a backbone Area with backbone routers
- all areas are connected to the backbone
- each router is connected to two or more areas is called an area border router and is also part of the background
- if there is only one router out of an area it is called a stub area
- shortest path algorithms are used in an intra area sense and inter area sense
- find shortest path from area to area
- find shortest path from any host/node within an area to another within the area or from border router to any node in area
- exchange info between adjacent routers, but designates one router as the designated router to be adjacent to all other routers to exchange information so information not duplicated with one backup
- Message types listed in the following diagram
- BGP - The Exterior Gateway Routing Protocol
- BGP(Border Gateway Protocol)
- between ASes
- example policies gateway protocols can handle
- Do not carry commercial traffic on educational network
- don't send information from pentagon through iraq
- use TeliaSonera over Verizon
- don't use AT&T in Australia
- Apple traffic doesn't transit through Google
- ISP pay other ISPs to deliver packets, buy transit service
- interconnections called IXPs(Internet Exchange Points)
- ASes can do peering where they send each others traffic for free
- Multihoming
- company networks connected to multiple ISPs as backup
- Path Vector Protocol
- instead of maintaining routes, maintain path to next hop router and sequence of AS that route followed
- BGP communicates using TCP connections
- iBGP, eBGP internal or external BGP protocol
- internal every router at boundary learns all the routes seen by other boundary routers
- strategies
- routes via peered networks chosen in preference
- routes via shortest path chosen
- routes with lowest cost
- early exit or hot potato routing
- tends to make routes asymmetric
Internet Multicasting
- processes that send from one to a large number of viewers
- IP supports this due to range of IP addresses
- IGMP(Internet Group Management Protocol)
- every about once a minute hosts on LAN reports to a multicast router to identify which group they belong to
- PIM(Protocol Indpendent Multicast
- build spanning tree for multicast
- dense mode pruned reverse path forwarding used
- sparse mode similar to core based trees
Mobile IP
- goals
- each mobile host must be able to use home IP anywhere
- software changes to fixed host not permitted
- not permitted to change router software and tables
- packets should not make detours
- should not have overhead when mobile host is at home
- setup a home agent when roaming
- obtains a new IP address when in a foreign site
- packet for mobile arrives to home, it will tunnel to new site so mobile can send and reply using its home address instead of where it is at currently
- options to solve ip address issue
- create route to specific prefix at moving site, but too many sites possible
- change IP address of mobile, handles mobility at a higher level but breaks some applications whenever mobile moves
- mobility can be solved at link layer
- same as 802.11 wireless network, but degree of mobility is very limited
- IPv4 solution given in RFC 3344
- mobiles uses DHCP to get care of IP address at foreign location, finds an agent to get address from using ICMP
- tunneling achieved using proxy ARP to intercept packets
- Ingress filtering
- a security measure to discard addresses that are incorrect, but mobile will have foreign IPs so mobiles have to use care of address to tunnel packets to home location
- flying router on airplanes is different kind of mobility where the entire network is mobile
Subscribe to:
Posts (Atom)